WATLOWCLS200 Communications Specification Includes CLS200, MLS300 and CAS200
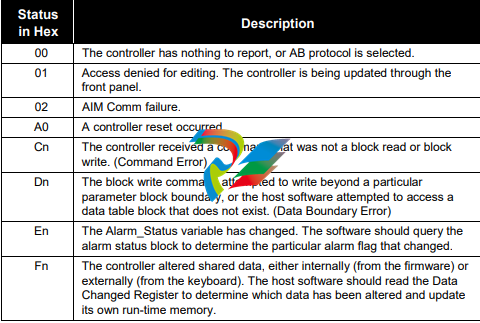
the controller is being updated through the front panel (0x1).
TNSL least significant byte of the transaction number. This is the first half of a “message stamp.” The
controller sends back the TNSL and TNSH exactly as it received them, so host software can use the
TNSL and TNSH bytes to keep track of message packets.
TNSH most significant byte of the transaction number. This is the second half of the “message stamp.
ADDL the low byte of the beginning data table address of the block of data to read or write.
ADDH the high byte of the beginning data table address of the block of data to read or write.
DATA the new values to be set with a write command, or the requested data in a response to a read
command.
DLE ETX ends every packet of information. Signals the end of a transmission.
BCC or CRC one or two-byte error check at the end of the packet. There are two error check methods:
Block Check Character (BCC), which requires 1 byte, and Cyclic Redundancy Check (CRC), which
requires 2 bytes.
Error Checking
The default error check method, BCC is easier to implement than CRC, and is acceptable for most
applications.
Select one error check method and configure both software and controller for that method, or they will
be unable to communicate.
The error check methods work this way:
Block Check Character (BCC)
BCC checks the accuracy of each message packet transmission. It provides a medium level of security.
The BCC is the 2’s complement of the 8-bit sum (modulo-256 arithmetic sum) of the data bytes between
the DLE STX and the DLE ETX. (1’s complement +1)
• BCC does not detect transposed bytes in a packet.
• BCC cannot detect inserted or deleted 0 values in a packet.
• If you have sent 0x10 as data (by sending DLE 0x10) only one of the DLE data bytes is included in
the BCC’s sum (the DLE = 0x10 also).
For instance, the block read example shown in the examples section, adds 0x08 00 01 00 00 80 02 10.
Note that the 0x10 representing DLE has been left out of the calculation. The sum should come to 0x9B.
1001 1011 = 0x9B
0110 0100 = 1’s complement
______ +1 = 2’s complement
0110 0101 = 0x65
Cyclic Redundancy Check (CRC)
CRC is a more secure error check method than BCC. It provides a very high level of data security. It can
detect:
• All single-bit and double-bit errors.
• All errors of odd numbers of bits.
• All burst errors of 16 bits or less.
• 99.997% of 17-bit error bursts.
• 99.998% of 18-bit and larger error bursts.
The CRC is calculated using the value of the data bytes and the ETX byte. At the start of each message
packet, the transmitter must clear a 16-bit CRC register.
When a byte is transmitted, it is exclusive-ORed with the right 8 bits of the CRC register and the result
is transferred to the right 8 bits of the CRC register. The CRC register is then shifted right 8 times by
inserting 0’s on the left.
Each time a 1 is shifted out on the right, the CRC register is Exclusive-ORed with the constant value
0xA001. After the ETX value is transmitted, the CRC value is sent, least significant byte (LSB) first.
Structured English procedure from AB Manual
data_byte = all application layer data, ETX
CLEAR CRC_REGISTER
FOR each data_byte
GET data_byte
XOR (data_byte, right eight bits of CRC_REGISTER)
PLACE RESULT in right eight bits of CRC_REGISTER
DO 8 times
Shift bit right, shift in 0 at left
IF bit shifted =1
XOR (CONSTANT, CRC_REGISTER)
PLACE RESULT in CRC_REGISTER
END IF
END DO
END FOR
TRANSMIT CRC_REGISTER as 2-byte CRC field
Examples
The host software sends two kinds of commands: block reads and block writes. This section shows
examples of both commands.
Note: If you read data from a loop set to SKIP, the controller will send an empty packet for that loop.
This section does not show how to calculate the error check value included with every packet. For help
calculating the error check value, see the section on BCC or CRC.
Block Read
This example shows the block read command the host software sends, the controller’s responses, and the
software's acknowledgment.
Situation: Read process variables for loops 1 to 8.
• 8 process variables 2 bytes each = 16 bytes from data table address 0x0280.
Block Write
This section describes the block write command.
This example shows the block write command the master sends, the controller's responses, and the
master's acknowledgment:
Situation: Write setpoint of 100 to loop 6.
• 1 setpoint 2 bytes per setpoint = 2 bytes to address 0x01CA (0x01C0 + xA, a 10-byte offset).
• Character values are represented in hexadecimal.
• The sender is device address 0.
• The destination is device address 8 (controller address 1).
• The software sends transaction number 00.
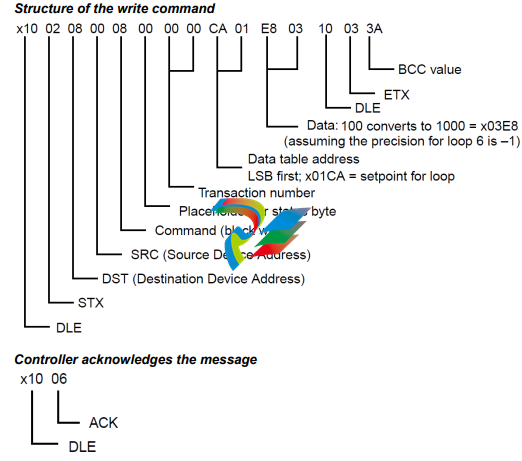
Message Data
Some messages contain data. What the data is and how much depends on the command used and the
purpose of the message.
Data for a Read Command
For a block read command, the data block consists of one byte that indicates the number of bytes to read
(up to 244 bytes of data). The controller sends back a packet with a data block that contains the
requested bytes.



































.png)

.png)

























.png)