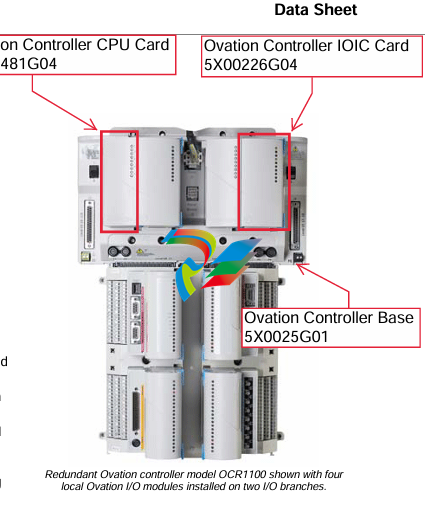
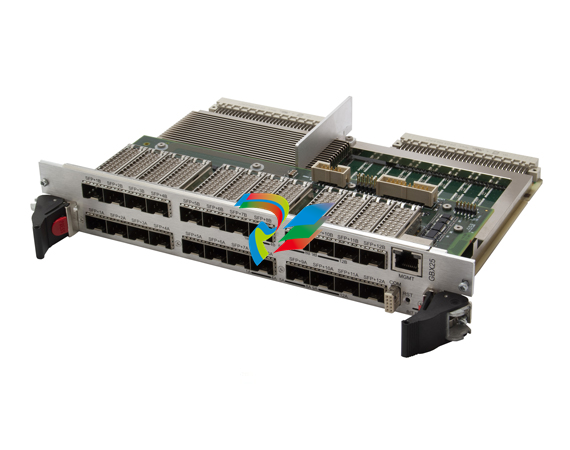
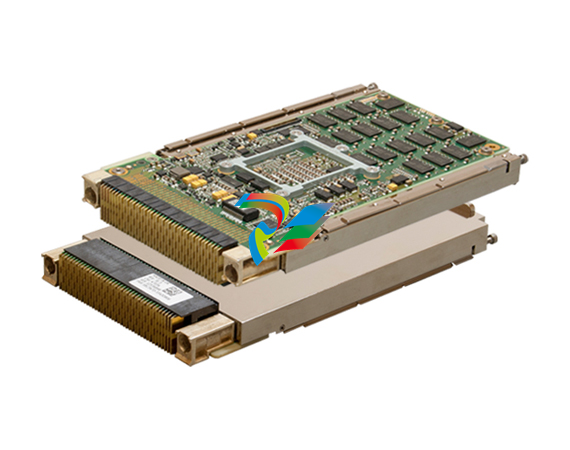
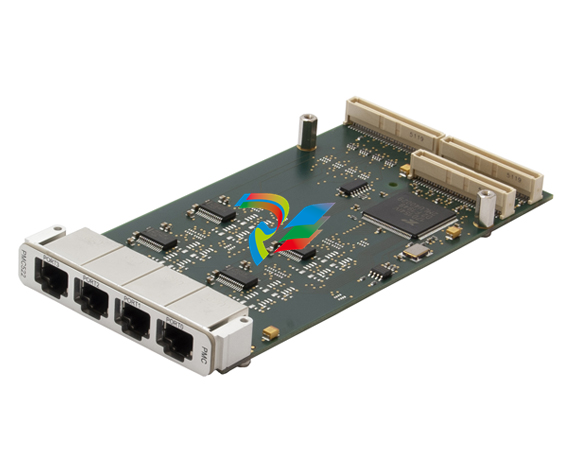
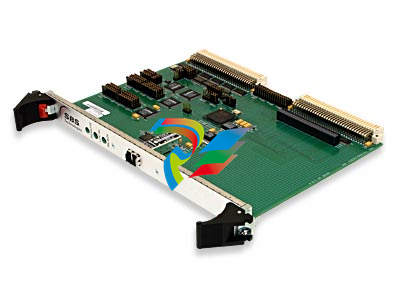
parkerVM600Mk2 A Second-Generation Architecture for a New Era
remote facilities – such as offshore
platforms – where remote access to
data was in highest demand.
For years, they had led the way
in the defining the features and
functions required of condition
monitoring and machinery
protection platforms because their
processes were often worth millions
of dollars per hour and machinery
failures were potentially so costly.
As such, they were the ones with
the most sophisticated needs and
the deepest pockets to address
those needs.
But then, the world began to
shift as the most pressing needs
began to fall within the power
generation sector along with
corresponding expenditures to
ensure cybersecurity therein.
Where a cyberattack might be
able to bring down a single
petrochemical facility, a similar
attack could potentially bring down
major portions of the electrical
grid in a country, affecting tens of
millions of people for days.
The Northeast blackout of 20034
,
for example, left 55 million
people in the US and Canada
without power – some for as long
as two weeks. A similar event
in Europe just a few months
later left 56 million people in
Italy and Switzerland without
power5
. Moving to the southern
hemisphere, a 1999 event in Brazil
lasted more than three months and
impacted 97 million people. And
a 2012 blackout event in India7
affected more than half a billion
people for two days. The point
here is that cyber vulnerabilities
in the power generation sector
are particularly serious because
they may not necessarily
isolate themselves to a single
facility; because the generation,
transmission, and distribution
infrastructure is interconnected
via a grid, an attack can impact
huge portions of the electrical
grid for days, weeks, or months at
a time. This also impacts critical
infrastructure such as hospitals,
law enforcement, banking, water
utilities, grocery stores, petrol
stations, and other entities that
depend on electrical power to
deliver vital goods and services.
The stakes are indeed exceedingly
high.
Coupled with the realization that
an attack on the power grid had
such devastating implications,
industry began to face the reality
that cyberattacks were not just able
to exploit conventional computer
systems – they could exploit
industrial control and automation
platforms such as SCADA systems
and PLCs. In 2007, the Aurora
Generator Test8
conducted by
Idaho National Labs demonstrated
that it was possible to compromise
a protective system via the
internet and thereby destroy a
diesel generator within a mere 3
minutes. Several years later, the
Stuxnet9 worm showed the world
that an industrial cyberattack was
no longer just hypothetical – it had
actually been accomplished. Iran’s
nuclear program was sabotaged by
Stuxnet-infected PLCs, destroying
the enrichment centrifuges they
controlled by sending them into
overspeed conditions.
All of this is to underscore that
cybersecurity moved from not
even being on customers’ radar a
mere 15 years prior, to being their
number one concern by 2015.
While the VM600 had unwittingly
addressed a portion of these
concerns by entirely segregating
the protection functions from the
condition monitoring functions,
there were other aspects of the
system that represented cyber
vulnerabilities – vulnerabilities that
would require a new generation of
modules.
4 “Technical Analysis of the
August 14, 2003, Blackout: What
Happened, Why, and What Did We
Learn?”. North American Electric
Reliability Council. July 13, 2004.
Retrieved September 18, 2021.
5 “Report on the blackout in Italy on
28 September 2003” Swiss Federal
Office of Energy. November 2003. 6 “Wide Power Failure Strikes
Southern Brazil”. The New York
Times. March 12, 1999. Retrieved
September 18, 2021.
7 “India blackouts leave 700 million
without power”. The Guardian. July
31, 2012. Retrieved September 18,
2021.
8. “U.S. video shows hacker hit
on power grid”. USA Today.
September 27, 2007. Retrieved
September 18, 2021.
9. Kushner, David. “The Real
Story of Stuxnet”. ieee.org. IEEE
Spectrum. February 26, 2013.
Retrieved September 18, 2021.
Integration
While the separation between
protection and condition
monitoring in the legacy VM600
architecture was desirable from
the standpoint of cybersecurity, it
was not optimal in other respects.
In particular, because there was
no communication at all between
the condition monitoring and
protection environments, it was
cumbersome to see the status of
the protection system alarms from
within the condition monitoring
software.
Also, the same measurements
(such as overall amplitude or 1X
amplitude) were generated in each
path (protection and condition
monitoring) but could be slightly
different due to different circuitry in
different cards. Work-arounds were
available but the environments
for viewing protection and
condition monitoring statuses and
information were not truly unified.