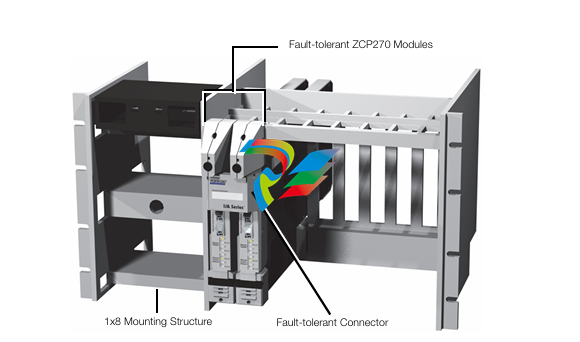
Ensuring Cyber Resiliency for OT Systems
The tie-in with cyber resilience is Mitsubishi Electric’s push to bring these security efforts to CC-Link and TSN. “By combining the networks” Kok continued, “there are little things that we take for granted. When you make a device that is compliant with our protocol, you get SNMP [simple network management protocol] support in the device as well. And SNMP lets IT systems ping and communicate with all kinds of endpoint devices. Those endpoint devices used to be isolated on a control network but are now exposed because they’re on a combined network.”
There is greater access to information. “It gives you greater ability to manage all the devices on your network,” said Kok. “Cybersecurity tends to be more important in that world. We're creating the opportunity for smarter machines because you have better communications with every aspect of the machine from its control devices to its PLCs [programmable logic controllers.
Abilkasimov said the cybersecurity threat landscape is continuously evolving, and as a next step organizations should validate if their cybersecurity controls can respond to their current environment or threat landscape. Schneider Electric’s cybersecurity resiliency approach is multifaceted. “This strategy starts at the top. The cybersecurity objectives are set by the Global CISO [Chief Information Security Officer], and the implementation of the strategy is carried out by the executive management team as a whole. A key element of the initiatives are the employees, so the resilience strategy includes robust training and education of all its employees. The strategy company-wide, risk-informed approach that has preventative (breach readiness) and response (breach resilience) measures in place for potential incidents,” he said.
Schneider’s program includes:
Employee training and awareness: The company aims to raise employee cybersecurity awareness, provide relevant training and create a culture to empower employees across IT and OT to act in a secure manner. The training includes an annual baseline awareness course for all employees and role-based trainings for specialized populations including cybersecurity site leaders.
Enterprise risk management (ERM) framework: Schneider Electric categorizes and translates cybersecurity risks into business and operational scenarios and exposure. This exposure is communicated with the C-suite to drive investments in risk mitigation initiatives. This framework is aligned to National Institute of Standards and Technology (NIST) Cybersecurity Framework and increases the company’s overall level of cyber resilience.
Incident response capabilities: Schneider Electric is constantly testing and improving its capacity to respond to operational disruption, damage to customers, compliance issues and IP theft. Its incident response plans are defined, and stress-tested routinely to ensure preparedness. The Security Operations Center (SOC) operates 24/7/365 and is staffed with security analysts leveraging security incident and event management (SIEM) capabilities with OT scenario-based playbooks and responders.
Crisis simulation exercises: Crisis simulations aim at training senior executives through operational roles, enhancing external collaboration and internal coordination and reviewing internal processes around crisis resolution. The company’s simulation activities follow a comprehensive framework with realistic and risk-based scenarios for the best outcomes and learning. The goal is for simulations go beyond testing and training and focus on examining and improving operational processes while enhancing readiness for future crises through experiential learning.
The combination of these programs ensure that cybersecurity risk is not an afterthought for the organization but rather an intentional practice to ensure cybersecurity resilience.
“Dragos emphasizes the importance of understanding the specific threats and vulnerabilities that could impact critical systems and assets and ensures that important context is built into its technology,” said Tonkin. “This begins with a thorough assessment to identify the ‘crown jewels’ or most critical components of an organization’s operations. Based on this assessment, Dragos advocates implementing controls that are proportionate to the actual threats and vulnerabilities identified.”
For example, a prominent water utility, responsible for managing 20 dams and 2,000 kilometers (1,243 miles) of pipelines, recognized the critical nature of its infrastructure and took steps to adopt a proactive cybersecurity stance to get ahead of potential threats. Audits pinpointed areas that needed improvement, raising leadership’s awareness of the importance of OT cybersecurity.
When seeking a cybersecurity provider, the utility prioritized OT-specific expertise and reputable providers. The water utility adopted the Dragos OT cybersecurity platform to streamline and advanced its cybersecurity programs to ensure the secure delivery of water to more than 5,000 commercial customers and enable critical projects in collaboration with industry, mining and government agencies.
.jpg)


































































.jpg)
.jpg)





.jpg)



.png)
.jpg)

.jpg)
_lVjBYb.jpg)

.jpg)
.jpg)



.jpg)
.jpg)







.jpg)

.jpg)
.jpg)